end-to-end encryption works
Picture opening up your main door broad as well as welcoming the world towards pay attention know your very most personal discussions. Unthinkable, straight? However, in the electronic world, individuals unintentionally leave behind doors ajar, possibly enabling cyberpunks, technology business, provider as well as safety and safety companies towards peek right in to their personal interactions.
A lot depends upon the requests you utilize as well as the file security requirements the applications support. End-to-end file security is actually an electronic protect for on the internet communications. It is utilized through a lot of the much a lot extra prominent message applications. Comprehending end-to-end file security is actually essential for preserving personal privacy in people's progressively electronic lifestyles.
While end-to-end file security efficiently protects notifications, it's not foolproof versus all of cyberthreats as well as needs individuals towards proactively handle their personal privacy setups. As a cybersecurity scientist, I think that constant developments in file security are actually required towards protect personal interactions as the electronic personal privacy yard develops. Lack of transparency affects AI systems generally
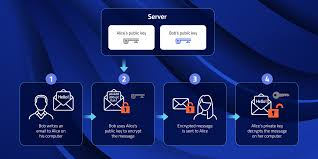
When you send out a notification through an application utilizing end-to-end file security, your application serve as a cryptographer as well as encodes your notification along with a cryptographic essential. This procedure changes your notification right in to a cipher - a jumble of relatively arbitrary personalities that hide real significance of your notification. end-to-end encryption works
This guarantees that the notification stays a personal trade in between you as well as your recipient, safeguarded versus unapproved accessibility, whether coming from cyberpunks, provider or even monitoring companies. Ought to any type of eavesdroppers intercept it, they will view just gibberish as well as will certainly not have the ability to decipher the notification without the decryption essential.
When the notification gets to its own location, the recipient's application utilizes the matching decryption essential towards open the notification. This decryption essential, safely kept on the recipient's gadget, is actually the just essential efficient in deciphering the notification, equating the secured text message rear right in to understandable style.