alert the devices’ owners to the danger
Cyber tools are actually absolutely nothing at all such as nuclear ones. They are actually easily industrialized as well as released through people as well as little teams in addition to conditions. They are actually quickly replicated as well as dispersed throughout systems, making difficult the really wish of everything that may be referred to as "cyber nonproliferation." Cyber tools are actually frequently released under a cloak of anonymity, creating it challenging towards determine that is actually truly accountable. As well as cyberattacks can easily accomplish a wide variety of impacts, the majority of which are actually turbulent as well as expensive, however certainly not devastating.
alert the devices’ owners to the danger
This doesn't imply cyber deterrence is actually doomed towards failing. The transparent range of cyberattacks needs that our team perform much a lot better towards prevent all of them.
Certainly there certainly are actually 3 points our team can possibly do towards enhance cyber deterrence: Enhance cybersecurity, utilize energetic defenses as well as develop worldwide standards for the online world. The very initial 2 of these steps will certainly considerably enhance our cyber defenses to ensure that even though an assault isn't deterred, it will certainly certainly not be successful.
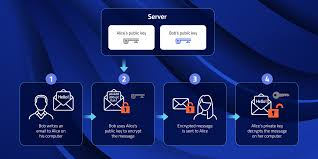
Cybersecurity helps deterrence mainly with the concept of rejection. It visits assaults prior to they can easily accomplish their objectives. This consists of beefing up login safety and safety, encrypting information as well as interactions, combating infections as well as various other malware, as well as maintaining software application upgraded towards spot weak points when they're discovered.
the most dangerous ramification of deepfakes
However much more essential is actually establishing items that have actually couple of if any type of safety and safety susceptabilities when they are actually delivered as well as set up. The Mirai botnet, efficient in producing huge information floodings that overload web web hosting servers, takes control of gadgets that have actually gaping safety and safety openings, consisting of nonpayment passwords hardcoded right in to firmware that individuals can not alter. While some business like Microsoft spend greatly in item safety and safety, others, consisting of numerous Internet-of-Things suppliers, don't.